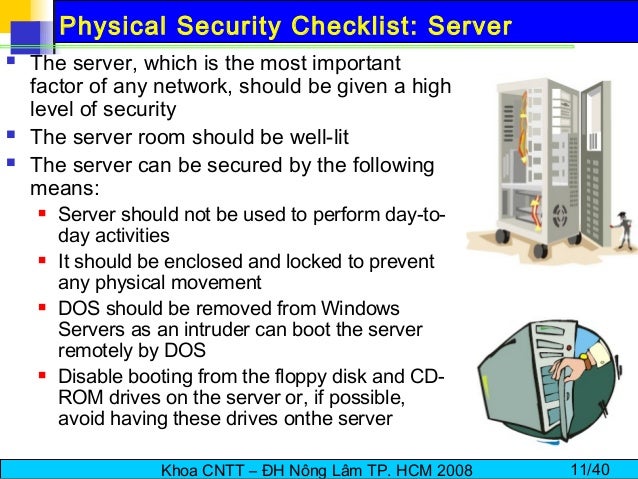
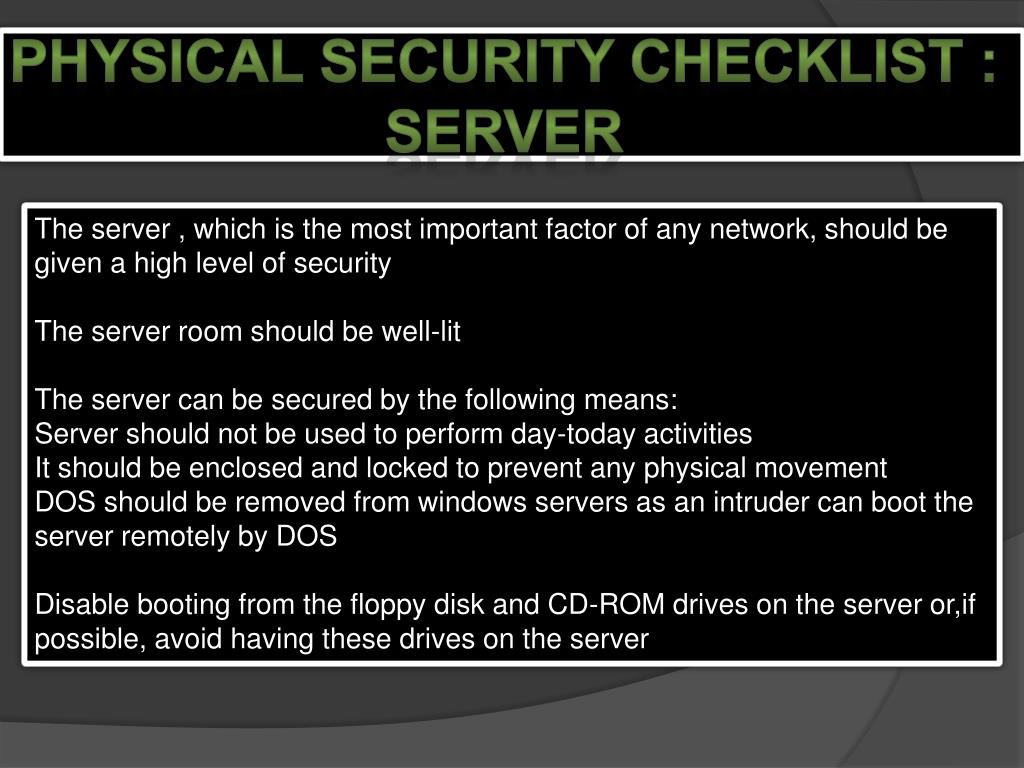
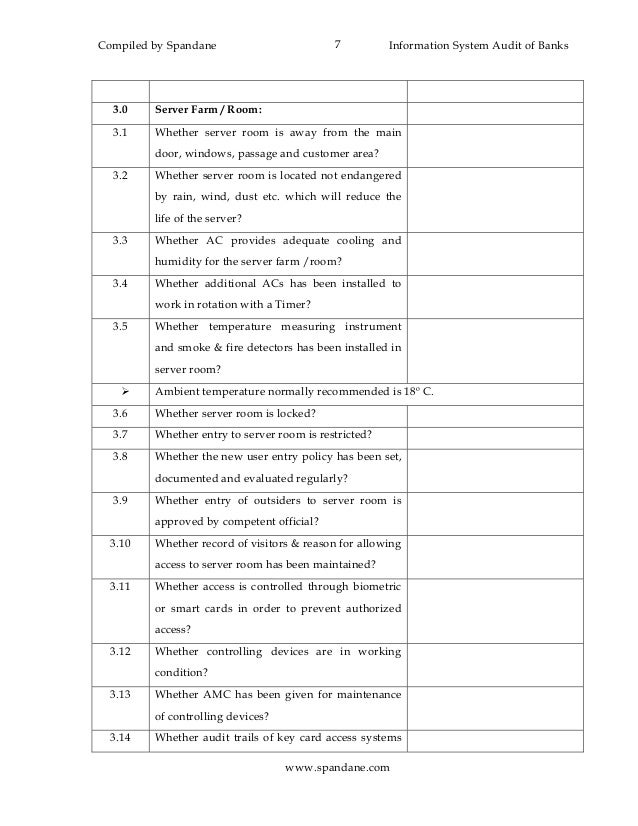
This paper presents an informal checklist compiled to ascertain weaknesses in the physical security of the data centers that their organization utilizes.
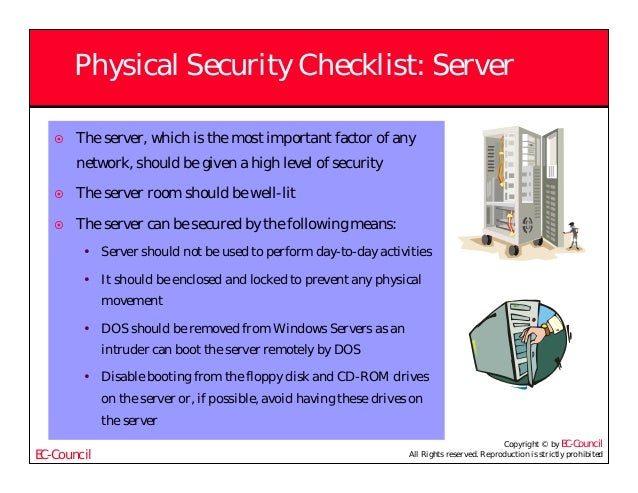
Physical security checklist server room.
Kisi s system is designed for it security teams and includes features like 2fa and sso for your doors.
This control enhancement provides additional physical security for those areas within facilities where there is a concentration of information system components e g server rooms media storage areas data and communications centers.
Securing the actual physical location of the server is one of most important parts of any server security process that s why it s first in this checklist.
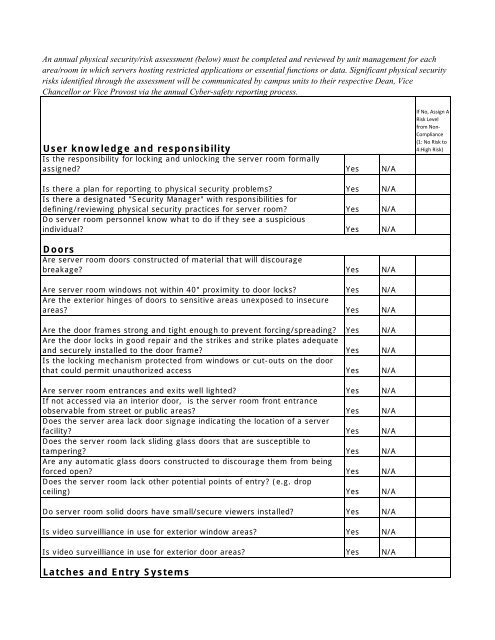
Introduction physical access to information processing and storage areas and their supporting infrastructure e g.
We ve outlined the steps in the sub checklist below.
Data center physical security checklist sean heare december 1 2001 abstract this paper will present an informal checklist compiled to raise awareness of physical security issues in the data center environment.
Physical security audit checklist performing regular security audits is a best practice that every business should follow.
Enacting a security checklist.
The key to a secure server room is ensuring the safety and security of the information and guarding against physical attacks by restricting access.
Every individual that has access to the room should have their own access code or card for entry.
Your server room needs access cards.
Data center physical security checklist by sean heare december 1 2001.
A physical security checklist for your data center by darren watkins 31 august 2016 no matter how simple or complex the security system it needs to be tested regularly to ensure it works as expected.
In order to protect your computer servers from serious issues you should make security your first priority when you re preparing a dedicated server room.
This document suggests controls for the physical security of information technology and systems related to information processing.
The concept is simple just like virtual access physical access must be as secure as possible.
The server room is the heart of your physical network and someone with physical access to the servers switches routers cables and other devices in that room can do enormous damage.













.png)